Windows 10 is Reaching End Of Life!
Are You Ready?
If you're still using it, your business could be exposed to serious risks!

Windows 10 reaches End Of Life on the:
14th October 2025

After this date, Microsoft will no longer provide security updates, patches, or support for Windows 10 or any older versions. This means systems running on Windows 10 or below from the 14th October 2025 will become increasing vulnerable to security threats and cyber risks.
What does End Of Life Mean?
End Of Life refers to the point when Microsoft stops supporting a particular version of Windows. Once this happens:
No more security updates will be released
Any newly discovered vulnerabilities will not be patched
Your device may be exposed to viruses, malware and data breaches
There may be bugs in the future which won't get fixed, or compatibility problems with other software/hardware.

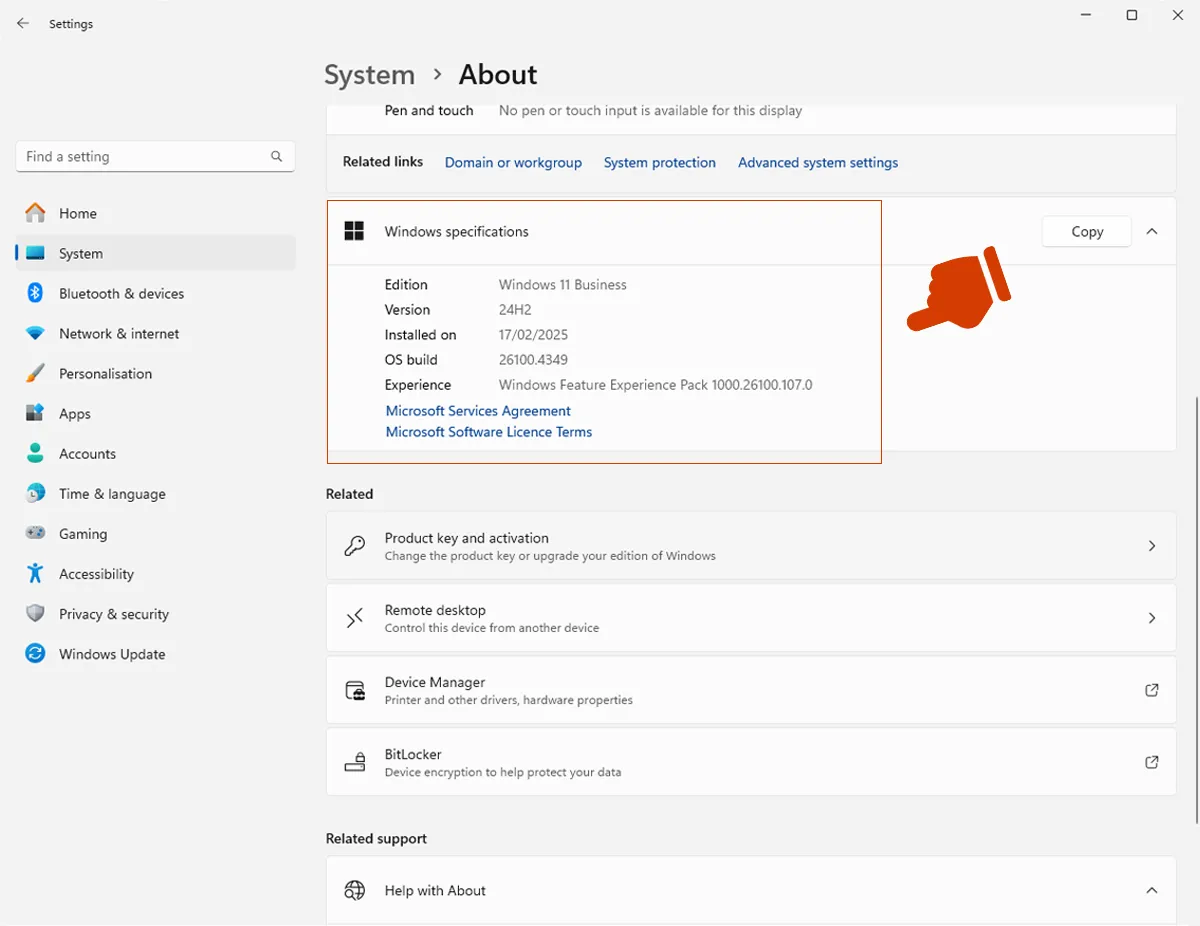
Is your Device running Windows 11?
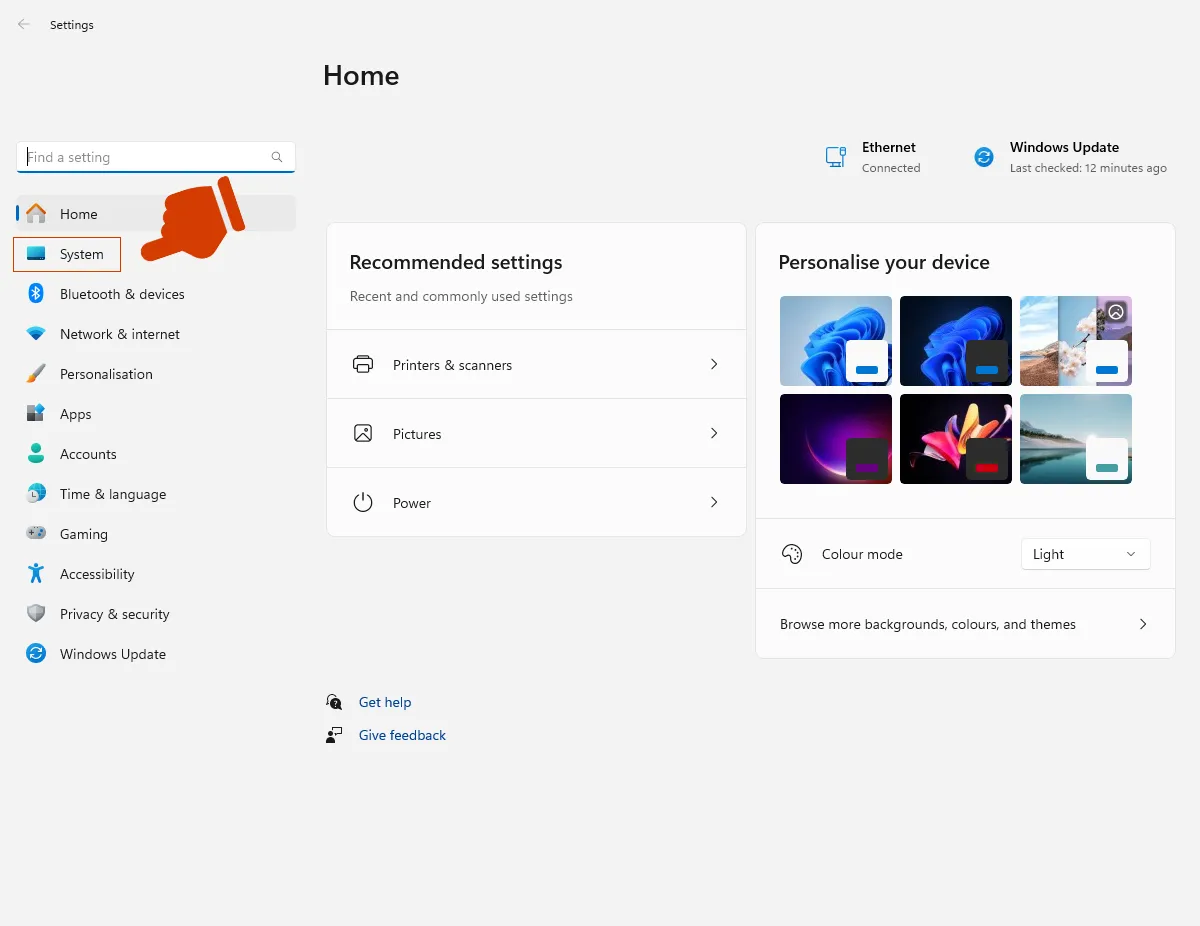
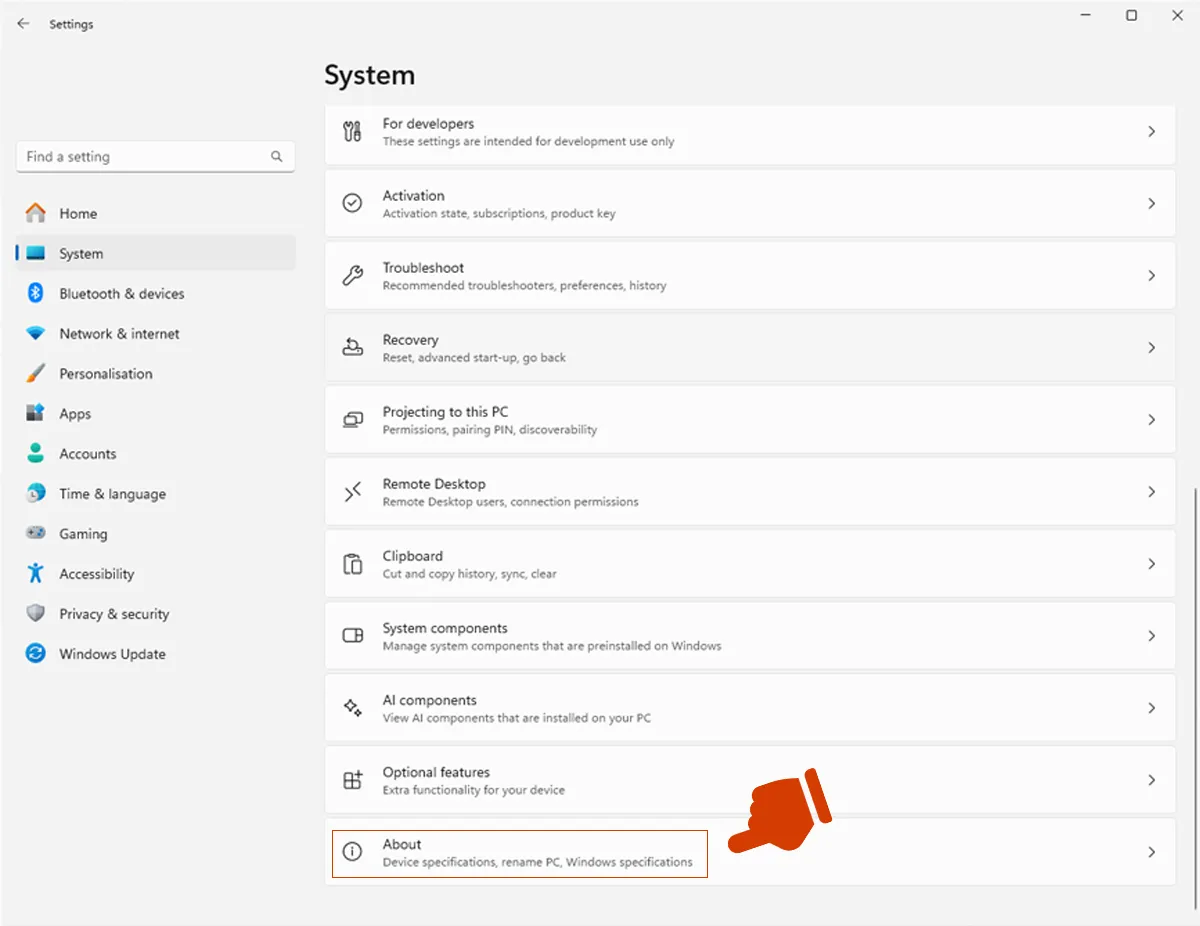
To check your system version:
Select Start > Settings > System
Then select About
You'll see your Edition, Version, and OS Build information there
What Happens When You Ignore End Of Life?

End Of Life doesn't just mean the end of updates, it means the beginning of risk.
Across the whole world, some of the most devastating cyber attacks in history were made possible because businesseses continued to use outdated , unsupported systems. When Microsoft stop releasing updates, vulnerabilities remain exposed and cybercriminals will take full advantage.
Cyber Security Incidents from using End-Of-Life Windows Versions.
The Windows 7 to Windows 10 transition.
Microsoft ended supported for Windows 7 on January 14th 2020. From this date, it stopped releasing all security updates for it. This means that any new vulnerabilities that were discovered would remain unpatched on Windows systems. This effectively leaves "no door at all" in terms of defence. Despite this risk, a lot of people still continued to use Windows 7 after this date. In 2021, over a year after Windows 7 reached End of Life, there was still an estimated 200 million computers that were running Windows 7. Organisations using End of Life systems face not only technical vulnerabilities but also compliance and legal risks. Running ourdated systems can violate regulations including GDPR and lead to penalties.

Below, we will explore notable security risks that effected Windows 7 devices, the impacts invollved, and the lessons learned to prevent these incidents in the future.

Notable Incidents and Timeline of Attacks:
Even before Windows 7 reached End of Life, cyber attacks exploiting outdated Windows systems provided a grim preview of the risks. Hackers have repeatedly leveraged known weaknesses in unsupported or unpatched Windows versions to wreak havoc. Here is a timeline of key cyber security incidents and major cases related to the Windows 7 End of Life period:

-
May 2017: WannaCry Ransomware Outbreak
Global ransomware attack exploits a Windows SMB vulnerability; 98% of infected PCs ran Windows 7.
-
Summer 2019: "BlueKeep" Exploit Weaponized
Attackers abuse an RDP flaw affecting Windows 7 and older systems to infiltrate networks..
-
January 2020: Windows 7 Support Ends
Microsoft stops security updates for Windows 7.
-
August 2020: FBI Issues Warning
Private Industry Notification warns of hackers targeting Windows 7 EOL systems, citing recent exploits.
-
February 2021: Oldsmar Water Plant Attack
Intruder remotely adjusts chemical controls via an outdated Windows 7 PC and remote access software.
-
January 2023: Extended Support Ends
Microsoft’s last Extended Security Updates for Windows 7 cease, fully retiring the OS after 14 years.
-
August 2023: LockBit Breaches Zaun Ltd
Ransomware gang steals data by compromising a “rogue” Windows 7 machine on the manufacturer’s network.
The WannaCry Ransomware Outbreak (2017)
The WannaCry attack in May 2017 was a perfect example of how devastating Windows vulnerabilities can be. This ransomware worm spread rapidly throughout the world as it exploited EternalBlue, which was a flaw in the SMB file-sharing protocol on Windows. Even though Microsoft had issued a patch in March 2017, many organisations (and all of the Windows XP systems, which were already unsupportred) had not applied it. This outbreak ended up being one of the largest cyber incidents to date. Hospitals, businesses and government agencies in over 150 countries were affected. An astonishing 98% of computers that were infected by the WannaCry Ransomware Outbreak were running Windows 7 (Specifically unpatched versions). This just shows how attackers will captitalise on outdated systems.
In the UK, the National Health Service (NHS) were massively hard-hit. This is because it was especially reliant on legacy Windows systems. With this attack, over 19,000 patient appointments and operations were cancelled. The NHS also suffered an estimated £92 Million in damages and IT recovery costs.
Oldsmar Water Treatment Facility Breach (2021)

One of the most alarming End of Life incidents occured in February 2021 on a Water Treatment Plant in Florida. In this attack, an unauthurised attacker gained access to the Oldsmar Water Treatment Facilities contreol and attempted to dramatically raise the level of Sodium Hydroxide in the water supply. This act would have then poisoned residents relying on this Water Treatment Facility. This breach was traced to a computer running Windows 7 that was being used to control operations. After an investigation, they found that this breach likely exploited multiple security weaknesses. They found that the team were running Windows 7, had poor password, and possibly had a remote desktop sharing tool exposed. By taking advantage of these weaknesses, the attacker took romote control of the system. They even moved the mouse and changed systems in real time. Fortunately, a plant operator observantly noticed the cursor moving. They then quickly reversed the chemical dosage changes which averted the harm. This near miss highlights that continuing to run End of Life systems in critical infrastructure can directly endanger public safety.
LockBit Ransomware Attack on Zaun Ltd (2023)
A more recent example on an attack on End of Life systems occured in August 2023. This is when the LockBit ransomware gang infiltrated the network of a UK perimeter fencing manafacturer. According to the company's official statement, this breach originated from an outdated Windows 7 PC that was connected to a manufacturing system and running specialised software. Although Zaun had taken measures to secure the network, it was confirmed that this unpatched machine was the point of compromise. From this attack, approximately 10GB of data was stolen by the criminals. Zan confirmed that whilst the beach was confined to that single device, there was a possibility that some network files were accessed. They later pubished the stolen data on LockBit's leak site after the company reportedly declined to engage with ransom demands.
This incident massively shows the ongoing risk which is posed by outdated operating systems, particually when they are still used in Operational Technology environments where upgrades can be technically or financially challenging. It also highlights the broader implications for cybersecurity, especially in sectors that support sensitive infrastructure.

What These Attacks Teach Us!
Outdated systems are magnets for ransomware
End of Life means no help from Microsoft, including no patches and protection
The cost of doing nothing far outweighs the cost of upgrading